You probably found yourself here because of a data breach. Whether you want to prevent one or you were caught in one you’ve come to the right place. This blog is broken down into three sections:
- Figuring out what data was exposed
- Going through remediation steps for each data point
- Preventing this from happening again
1: What Data Was Exposed?
First, you need to understand what data was exposed, this is crucial for your next steps to assess the real risks you’re up against. Start by making a list of data points that were definitely exposed, and then ones that may have been exposed.
To figure this out, start with official announcements made by the breached company. For example, if you were notified by Ticketmaster regarding their data breach, you would include the following data points: “phone number, encrypted credit card information as well as some other personal information”
What you’d write for 'definitely' impacted is:
- phone number
- credit card information
And for 'maybe' you'd write:
- first & last name
- billing address
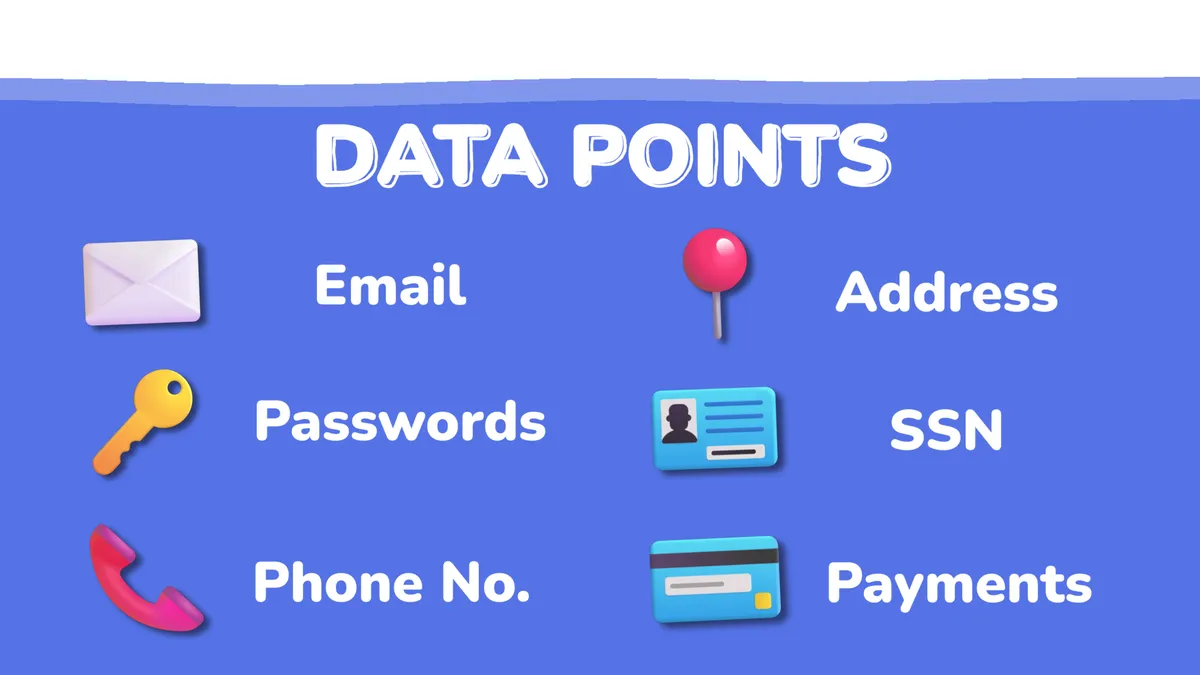
Generally, the most common data points you’ll find will include:
- Password
- Phone number
- Home Address
- SSN
- Payment info
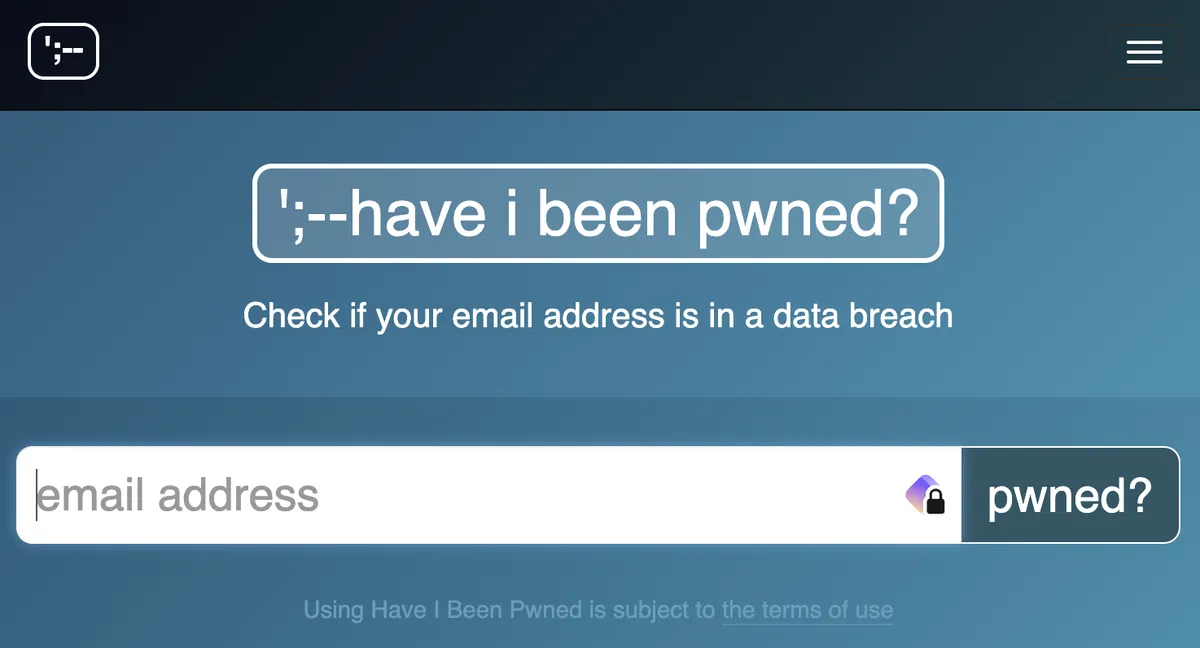
Now that you have a starting point with official announcements, what we want to do is cross-reference this information with trustworthy tools. I recommend using haveibeenpwned to check your email for data breaches and setting up notifications for your core emails.
You also want to keep up with coverage of your data breach as well. Not too long ago millions of people had their social security numbers leaked, and pentester was the site that you could use to see if your SSN was part of the breach. But not every breach follows the same script, so I’d suggest having a way to keep up with the latest news and updates. Shameless plug: I cohost a weekly podcast which begins with a data breach section where we do all this work for you. Check out Surveillance Report to learn more!
2: Remediation for exposed data
Now that you have a list of exposed data points, we can finally take action! Generally speaking: SSNs, passwords, and payment information are the most sensitive—so you’ll want to prioritize these breached data points and cross-reference those with your list you made from the first section. From there, take care of the remaining data points from the definitely and maybe sections respectively to decrease your likelihood of identity theft, fraud, and other malicious activity.

For example, with the Ticketmaster data breach from last section...I would go in the following order:
- payment information
- phone number
- home address
If an SSN was part of the breach, it would be the first thing you deal with. Prioritize accordingly so you don't do too much at once!
Now that you have a list of data points to target, I'm going to walk through remediation steps for every major data point. You do not need to follow every step, but I will lay out all the options you have to keep the level of safety flexible. To be thorough, you should always contact the breached provider to see if they have more specific advice for you as well.
🔐 Breached Passwords (Easy to Hard)
- The first critical thing you need to do is update the password on the breached account itself to prevent unauthorized access, very simple starting point.
- From there, make sure you’re not re-using your breached password. A tactic hackers use is called credential stuffing, where they take passwords from one data breach and try them on your other accounts. Myself and many security experts are proponents of safe password managers. I’ve been using Proton Pass and loving it. If you don’t like password managers, just make sure you have a system for saving secure and unique passwords.
- The final step to maximize protection is to enable multifactor authentication for your breached account and other sensitive accounts like your email. TOTP is a more secure multifactor method where you scan a QR code for temporary access tokens. If you want to take it to the next level, consider hardware keys for accounts that support it! The more services you enable multifactor authentication for the better, but at least try to cover your most sensitive accounts.
📥 Breached Emails (Easy to Hard)
- Make sure the security for your breached account is safe. Make sure that you update your password and enable any multifactor authentication security options on the breached account. Go back to the passwords section for password security advice.
- Make sure you secure your email account itself. Email accounts are valuable because they’re a central location for many of your sensitive accounts. To do this, make sure you’re not re-using passwords and make sure you’re using multifactor authentication on your email account.
- Be cautious with any phishing attempts, when someone spoofs a website to trick you into giving them your credentials. Now that your email is public knowledge you may receive more of these attempts!
- The fourth thing gets more advanced and isn’t for everybody, but it’s to compartmentalize emails for different things—the extent of which varies. Some people prefer a minimal approach where they have one email for their most sensitive accounts, a second email for the rest of their accounts, and a final email for spam and/or communication. This bucket approach is a nice convenient way to add a layer of separation between your accounts. Not only will a data breach not leak into your other email accounts, but you can properly prioritize security protocols by implementing the strictest security protocols on your more important email account(s).
- Some people like myself prefer to ditch the bucket method and opt to use a unique email for every service. This might seem like a lot of work, but there are aliasing services that make this easy. I’m using Proton Pass which auto generates aliases that forward to my normal email inbox. With this workflow, if an email is ever breached or someone shares it with a third party, you know exactly who is responsible since the email is tied to only one service. Some providers that offer aliasing include:
- Proton Pass
- Simple Login
- Addy.io
- Startmail
📱 Breached Phone Numbers (Easy to Hard)
- The first and most important thing is to be aware of phishing attacks, similar to the email section. Now that hackers know your phone number, you may receive texts or calls with the goal of getting more information from you. Be alert!
- I’d suggest logging in to your phone’s cellular account and making sure you utilize every security option available to you. Go back to the passwords section regarding secure passwords and multifactor authentication options.
- From here I recommend calling your cell provider to ask if they offer additional protections against sim swap attacks. These are when somebody impersonates you and convinces your cell company to re-issue your number to them, allowing them to intercept all of your messages and calls. Call your cell provider and see what they can do to prevent this!
- Another small but minor step is to avoid number-based accounts when you can. Many providers allow you to use an email instead of a phone number. It’s much easier to change emails in the event of a breach!
- From here phone numbers are going to look a lot like the email section of this video, using buckets to compartmentalize numbers for different things. The general buckets for most people will be:
- A phone number for communicating with friends and family
- A phone number for accounts
- A spam number
Services like Google Voice and MySudo can make this much easier and affordable!
👤 Breached Social Security Number (Easy to Hard)
- What you can do with your SSN is both free and takes you a long way, without ever needing a credit monitoring service. First, freeze your credit. This stops anyone from opening a new line of credit under your name, meaning you will need to actively remove the credit freeze next time you want to open a new line of credit. It has no drawbacks, it has no impacts on your credit score, and all it does is keep you safe. To do this just open an account with all three credit bureaus and place a freeze. All three have temporary credit lifts for when you want to apply for new credit, so you can temporarily lift the freeze for however much time you need it lifted. Everyone should do this, it’s the most important thing in this blog.
- From there, set up alerts on your credit file, make sure it’s always you who is responsible for anything happening.
- I’d recommend planting your flag and setting up official government accounts that use your SSN so you can claim the accounts before a hacker does. An example of this is the SSA website.
- Many people ask us about credit monitoring services...I'm generally opposed to them. They don’t tend to do anything that services like haveibeenpwned and paying attention to your credit accounts can’t do. Credit monitoring services at best just take your money, and at worst expose you to additional risks like their own data breaches. The only two benefits a credit monitoring service can provide that you can’t get yourself are a dedicated support agent if you need help in an emergency, and some offer liability insurance if you think that they’ll pay you in a situation where you experience financial loss. But neither of these should happen in the first place if you follow the steps in this blog.
💰 Breached Payment Information (Easy to Hard)
- Payment information is pretty important because well…it’ll cost you. The first thing I recommend is trying to avoid debit cards online when possible. Credit cards make it a lot easier to dispute and reverse transactions in a bad situation.
- From there, services like Apple Pay and Google Pay do a single layer of obscurity with your card number, which helps with data breaches since providers don't get access to your original card numbers.
- Be cautious with who you give your payment information to in the first place. Make sure websites are reputable, and if you have second guesses: use gift cards, either native gift cards like an Amazon gift card, or you can get a non-reloadable prepaid visa gift card to use on sites you have less faith in. Most of these can be purchased at your local convenience store.
- Payment processors like PayPal are also great when you don’t trust the site itself to handle your card information.
- Finally, what I do is I use privacy.com. Privacy.com let’s you generate dedicated cards as well as burner cards for every site. Use them on as many sites as possible so any data breach keeps your payment information isolated to that one site.
🏠 Breached Home Address (Easy to Hard)
A breached home address is a tricky one. Fortunately, most people don’t need to be super concerned with a breached home address unless they’re a person of interest. Most hackers are concerned with easy targets like people reusing passwords, they're not looking to physically go to your home. With that said:
- Keep an eye on online directories and people-searching sites to make sure your home address stays off of them. We’ll have a guide sometime in the future on how to opt out of data search websites, so stay subscribed to catch that.
- Be cautious of suspicious mail that like phishing attacks online are trying to get sensitive information from you.
- From there, I suggest basic home security. Like improving your locks, setting up alarms on your windows, being careful with package thefts, setting up cameras, and doing whatever you can to improve the security of your home.
- Finally, I recommend setting up a mailbox that’s away from your home that you use for anything that doesn’t require a residential address. Personally I go on Yelp and type in private mailbox in my area. This gives me results for local mailboxes that I can use for shipping things nearby to keep my address off of substantially more websites.

3: Prevention
With all of that out of the way, I wanted to consolidate 10 prevention steps everyone should do to prevent data breaches from happening in the first place. And if they do happen, they'll cause a lot less damage. Refer back to Part 2 of this blog for more specific information of each step:
- Freeze and monitor your credit, it’s the most important thing in this blog.
- Use a password manager or another method of securely storing unique passwords for each website
- Utilize multifactor authentication as often as possible, opting for more secure versions of multifactor authentication like TOTP or security keys instead of your phone number.
- Close accounts you no longer use, digital minimalism goes a long way and the less data and accounts you own, the better.
- On this note, use services that go out of their way to collect less data about you. Less data collected is less data to secure. Be wary of people asking for too much information.
- For emails, I recommend having multiple emails for different things. On a basic level, at least have an email for accounts separate from spam and the email you use for communication. But ideally you’re using an email aliasing service like the ones I covered earlier in the blog. Also make sure to lock down your email and keep it secure.
- Similarly, your phone number is something you should try to compartmentalize across a few different numbers. We discussed strategies for doing this earlier, and you also want to make sure your phone number is locked down.
- Make sure you’re being careful with your payment information online. Opt to use credit cards, Apple Pay, PayPal, gift cards, or ideally aliasing services like privacy.com to protect your payment information as best you can.
- Make sure all of your devices and software run the latest software with security patches.
- and finally……KEEP BACKUPS. In a worst-case scenario, someone can lock you out of sensitive data or even infect you with ransomware. Keep safe backups.
Summary
With all of that said, I hope that you feel empowered. This is all a spectrum, so if you only take care of the basics—that’s okay. While there’s always more you can do, my goal is for you to find the best compromise between safety and convenience. The work you put in today can save yourself literally months of headache in the future, so don’t underestimate how much your work right now can pay off. You being here puts you well ahead of the average person, and most people are looking for easy targets. Don’t be an easy target, make positive steps, and go sleep well tonight knowing you've taken some control of your digital life.
Stay informed on digital threats and how to fight back—delivered directly to your inbox.










Member discussion